- Only download attachments you are expecting and/or trust, from senders you know and trust.
- Heed any warnings from your antivirus application. If you receive an alert from your antivirus software, be thoughtful about whether or not to allow the action.
It is recommended that you share this reminder with your users.
What is CryptoLocker?
Ransomware is a type of malware which essentially holds access to an infected system hostage and then demands a ransom be paid to the culprits in order to reinstate a user's access. CryptoLocker is a new ransomware we have found threatening local businesses' by infecting user workstations. CryptoLocker is a hijacking application that is transmitted via e-mail. The executable application is downloaded via an e-mail attachment.
Upon download, CryptoLocker encrypts files on the workstation using AES 256-bit encryption, one of the highest levels of encryption available. It encrypts all local files, mapped network drives, and accessible drives and files over a VPN connection.
Cryptolocker is believed to be targeting businesses, encrypting those file types that are commonly used by business users. The targeted files have extensions such as: .odt, .doc, .docx, .xls, .xlsx, .ppt, .pptx, .mdb, .accdb, .rtf, .mdf, .dbf, .psd, .pdd, .jpg, .srf, .sr2, .bay, .crw, .dcr, .kdc, .erf, .mef, .mrw, .nef, .nrw, .raf, .raw, .rwl, .rw2, .ptx, .pef, .srw, .x3f, .der, .cer, .crt, .pem and .p12.
At this time, it appears that CryptoLocker's action is singular - to lock down the files and restrict access. There is no evidence as of yet that the infected files are being accessed or uploaded from the system.
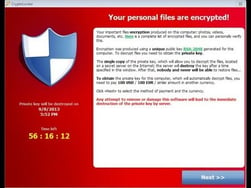
The targeted user rarely knows anything is amiss until it is too late. Once the encryption is complete, the user is virtually locked out of all files. To regain access, CryptoLocker uses a pop-up prompt directing the user to purchase a private decryption key, ranging from $100 - 300 USD. There is often a deadline provided to encourage the user to comply within a certain timeframe.
After diligently researching this virus, it appears that the malware can be uninstalled, but the encryption will remain. Once infected, a user's options are:
-
Remove the infection with your antivirus program and restore the encrypted files from a backup
-
Purchase the decryption software (paying the ransom)
If you have any questions regarding CryptoLocker or any malicious software concerns, please do not hesitate to contact Daystar's Professional Services Group immediately. E-mail support@daystarinc.com, submit a ticket in your client portal, or call support at 603.766.5924 x3.